Of the 40 or more EAP protocols available, Passpoint typically uses 3: EAP-TLS; EAP-TTLS & EAP-SIM. And, in coordination with EAP-TTLS, PAP or CHAPv2 can be leveraged.
In this post we’ll look at how GlobaReach uses EAP-TTLS, and how any security concerns are addressed – first some background on EAP.
EAP
Extensible Authentication Protocol (EAP), is used on encrypted Wi-Fi networks as a secure way to send authentication information. It:
- Provides the framework to use various authentication methods.
- Adapts to future security needs.
- Can be kept simple, if required.
EAP-TTLS – and why Globalreach uses it
EAP-TTLS offers an extensible security method, with certificate-based mutual authentication. However, unlike EAP-TLS, only the server side requires a certificate and can enable Wi-Fi networks to securely use and connect to alternative identity databases.
The main advantage? Easy management and disaggregation of personal data during authentication.
Using EAP-TTLS, GlobalReach:
- Keeps the user’s true identity separate from the user’s RADIUS authentication identity – in compliance with local identification laws.
- Can associate the Chargeable User Identity (CUI) with the user’s true identity, as well the RADIUS data store. Totally separate databases can be for extra security.
- Ensures that the RADIUS data store does not know the end user’s true identity, only whether the Chargeable User Identity (CUI) is allowed online.
- Configures the RADIUS authentication data store so that it only retains the randomised/anonymous username, password and an associated CUI – unless there is a requirement for a quality of service (QoS) profile to be associated.
The following diagram shows a typical EAP-TTLS architecture:
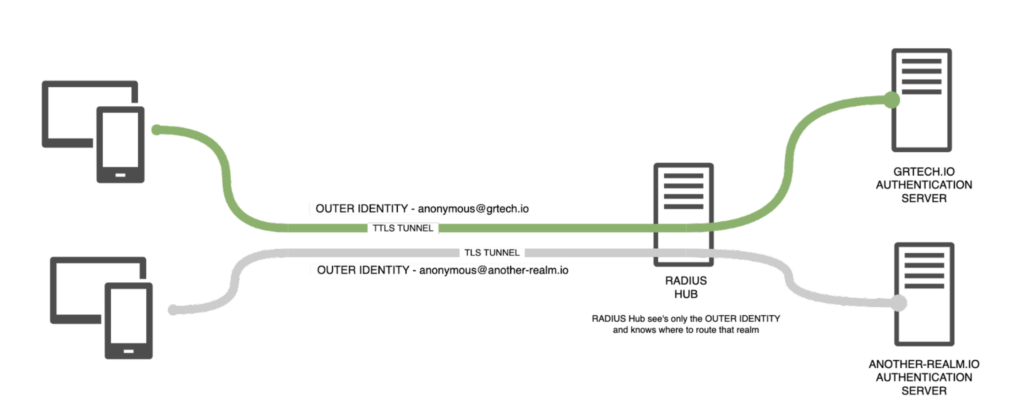
- The EAP tunnel Outer Identity is visible to any network operator in the path of the authentication request.
- This allows the network operator to direct the tunnel to the correct authentication server by using the outer realm.
- Typically, the Outer Identity for Passpoint authentication always uses the prefix anonymous@, as it has no use other than to denote where to route the request.
The main advantages of this architecture
- A user can be associated with multiple CUIs, and be changed in life without re-issuing a new profile.
- In the event of a legal request, the CUI can be released and associated with any RADIUS access logs depending on how the network is deployed, as required.
- The CUI can be passed to the owner of the true identity database to release information about that individual.
- The actual identity database doesn’t need to be exposed to GlobalReach – our customers retain the end-user’s identity at all times. (Our preferred policy is never to hold PII. )
Why the Security Concern?
Unless the more sophisticated and secure Inner Identify authentication method Challenge Handshake Authentication Protocol version 2 (CHAPv2) is used inside a TLS (v1.3) tunnel, (as GlobalReach does), a variation of the way EAP is used could lead to an Inner Identity being exposed by a sophisticated Man in The Middle (MiTM) attack.
This is because, when end-users connect to secure Wi-Fi networks, the identification data exchange happens inside a tunnelled EAP connection. If an insecure protocol, such as Password Authentication Protocol (PAP) is used for this exchange, security risks can follow.
The Advantages of CHAPv2
CHAPv2 creates a unique challenge phrase by generating a random string. It authenticates in such a way that static secret information is never required. The username and password are encrypted in transmission within the secured TTLS tunnel.
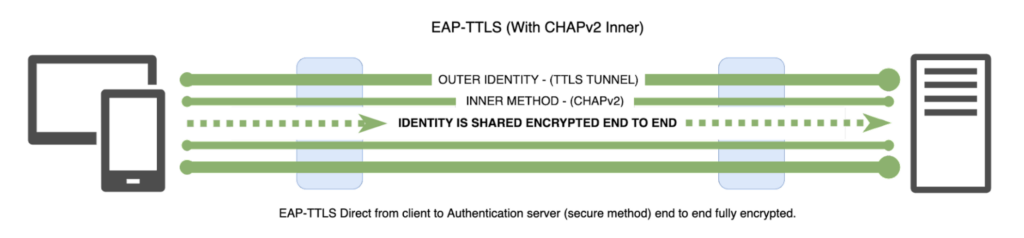
Compare CHAPv2 with PAP, and with EAP-TLS:
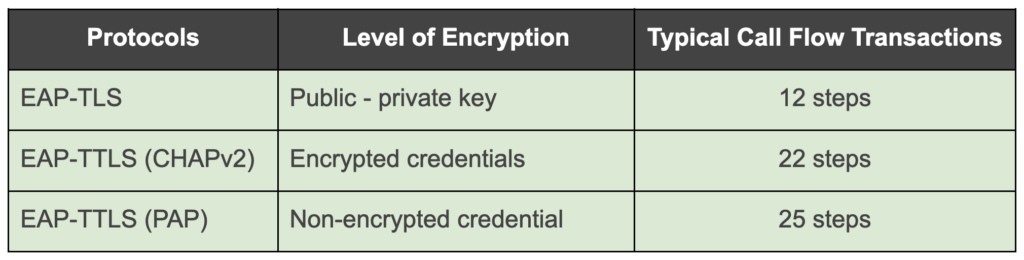
…but are There Drawbacks with CHAPv2?
CHAP could be brute-forced.
It would require a bad actor to sit within a network and authentication path, with access to the authentication server’s private certificate, to decode the outer identity.
GlobalReach chooses to use CHAP inside a TLS (v1.3) secured end to end tunnel. TLS is used by HTTPS across the internet and other network protocols for encryption, and is deemed secure.
And even if the bad actor was successful, GlobalReach’s disaggregation of the user’s identity would deliver a fake randomised username.
Conclusion
GlobalReach’s use of EAP-TTLS combined with CHAPv2 and TLS v1.3 tunneling offers an encrypted, highly secure, easily managed method of delivering Passpoint credentials. It enhances overall security by:
- Disaggregating a true identity from an authentication identity
- Using an EAP tunnel secured by a valid TLS (v1.3) certificate
- Incorporating encrypted inner authentication identities
- Enabling the optional use of RadSec to carry customer requests within a dedicated IPSEC tunnel.[6]
—-
GlobalReach is ISO27001 certified and is routinely independently audited by BSI, in addition, we hold a UK Cyber Essential accreditation and operate a company-wide Information Security Management System. Our Information Security commitment can be found here.

